Canadian agency compliance program
1 Version and Authorization
2 Objectives
This document represents Talk Remit’s Agent Compliance Program (“ACP”), specifically, the procedures that Talk Remit agents are required to comply with over the duration of their relationship with Talk Remit.
It is Talk Remit’s Money Laundering Reporting Officer (“MLRO”) responsibility to ensure that all new and existing agents are aware of and follow the requirements outlined within this ACP. The MLRO works together with the Agent Compliance Unit to assist agents in complying with these requirements.
This document addresses the following elements:
- A description of ML/TF
- Regulatory framework
- Penalties of non-compliance
- The role of the agent
- Training
- Customer onboarding and due diligence
- Regulatory reporting
- Suspicious indicators
- Record keeping and retention
3 Agent Compliance Program Requirements
In order to ensure compliance with the Proceeds of Crime (Money Laundering) and Terrorist Financing Act (“PCMLTFA”) and its regulations (together, the “Legislation”), Talk Remit developed this ACP and expects all agents to be subject to and adhere to its policies and procedures with no exceptions.
The ACP was developed to assist agents in understanding how to process transactions according to Talk Remit’s policies, recognize and escalate suspicious activity, identify high risk jurisdictions and to reiterate basic money laundering and terrorist financing (“ML/TF”) concepts.
The ACP is given to new agents upon approval and to existing agents that have been renewed. The MLRO or Agent Compliance Unit reviews the ACP with each agent to ensure a solid understanding.
The MLRO is responsible to keep the ACP up to date as regulations change. Any changes are communicated directly to all agents within a reasonable amount of time.
4 Overview and Regulatory Framework
4.1 What is Money Laundering?
ML is knowingly or recklessly dealing with the proceeds or property derived directly or indirectly as a consequence of an indictable offence, with the intent to conceal or convert any part of them. Concealment is a not necessary for an offence and conversion can be as simple as a deposit or a transfer.
There are three recognized stages in the ML process.
Placement: The placement stage represents the initial entry of the proceeds of crime into the financial system. This is the stage when money launderers are the most vulnerable, particularly if the proceeds are cash based, as they are more likely to raise suspicions of bankers and officials.
Layering: The layering stage can be complex and may involve multiple layers of financial transactions. This stage may involve transactions such as buying and selling international currency and money remittances (“EFT”), as well as multiple banks, people or legal entities. Layering of transactions disguises the audit trail as well as the original source and ownership of funds.
Integration: The final stage is where the laundered proceeds have achieved an air of legitimacy and can be safely integrated into the financial system. At this stage it can be very difficult to identify a link to the original proceeds of crime.
The ML process is continuous, with dirty money being introduced into the financial system continuously.
4.2 Methods of Money Laundering
There are many methods to launder money, and the schemes are becoming increasingly sophisticated and complicated where technology is opening new opportunities to move money quickly, seamlessly, and anonymously through new financial products and services. The following are some examples of common ML methods that MSBs are especially susceptible to.
Structuring: Structuring is where the illicit funds are broken into multiple/sequential transactions below the threshold which would require mandatory reporting or identity and record keeping requirements. Structuring is the most prevalent ML technique observed by FINTRAC in relation to MSBs.
Smurfs and Nominees: The use of nominees is one of the most common methods of laundering and hiding assets. In this scenario, a launderer uses family members, friends or associates to conduct transactions in their own names but on behalf of the launderer. Nominees are used to avoid attention and conceal the source and ownership of the funds. The coordinated use of nominees for the purposes of breaking down large value transactions into several “below threshold” amounts is a specific type of structuring called “smurfing”.
Informal value transfer systems: These can include hawalas, an Arabic word for a particular international underground banking system. The hawala includes the complete service from placement to integration. Similar services are provided under other names in other parts of the world, such as fe chi’en in China
4.3 What is Terrorist Financing?
TF provides the funds necessary for terrorist activity. The main objective of terrorist activity is to intimidate people or compel a government to do something. Terrorist activity is undertaken for political, religious or ideological purposes.
Terrorists need financial support to carry out their activities and achieve their goals. In this respect there is little difference between them and other criminals in their use of the financial system. A successful terrorist group, much like a criminal organization, is one that is able to build and maintain an effective financial structure, including sources of funding and means of hiding the links between those sources and the activities of the terrorist group.
The sums needed to mount terrorist attacks are not always large and the associated transactions are not necessarily complex.
4.4 Methods of Terrorist Financing
There are two primary sources of financing for terrorist activities. The first involves getting financial support from countries, organizations, or individuals. The other involves revenue-generating activities which may be linked to legal or criminal fronts.
The revenue generating activities of terrorist groups may include criminal acts, and therefore may appear similar to other criminal organizations. Kidnapping and extortion can serve a dual purpose of providing needed financial resources while furthering the main terrorist objective of intimidating the target population. In addition, terrorist groups may use smuggling, fraud, theft, robbery, and narcotics trafficking to generate funds.
Financing for terrorist groups may also include legitimately earned income; collection of membership dues and subscriptions, sale of publications, speaking tours, cultural and social events, as well as solicitation and appeals within the community. This fundraising might be in the name of organizations with charitable or relief status, so that donors are led to believe they are giving to a legitimate good cause. This type of “legitimately earned” financing might also include donations by terrorist group members of a portion of their personal earnings.
The methods used by terrorist groups to generate funds from illegal sources are often very similar to those used by “traditional” criminal organizations. Like criminal organizations, they have to find ways to launder the illicit funds to be able to use them without drawing the attention of the authorities. For this reason, transactions related to TF sometimes look a lot like those related to ML.
5 Regulatory Framework
In Canada, money services businesses (“MSB”) are subject to the Legislation related and must implement a compliance program that encompasses all the requirements under the Legislation.
The Financial Transactions and Reports Analysis Centre of Canada (“FINTRAC”) is the regulatory agency accountable for monitoring compliance with these laws in addition to receiving regulatory reports and conducting transaction analysis.
This ACP has been developed in accordance with the Legislation and regulatory guidance provided by FINTRAC.
5.1 Penalties of Non-Compliance
The failure of an MSB to implement and adhere to an effective compliance program can expose it to serious regulatory intervention and potentially affect its ability to conduct business. If FINTRAC observes compliance failures, it has the option to:
- apply monetary penalties, which range from $1,000 per violation to $500,000 per violation based on the severity of the failure; or
- refer offences for criminal prosecution with potential fines up to $2 million and/or imprisonment for up to five years.
As an agent of Talk Remit, failure to follow these policies and procedures could result in serious consequences. [1] It is therefore imperative that all agents have a clear understanding of the requirements laid out in this ACP and perform their duties with care and attention to detail.
6 Role of the Agent
Talk Remit relies on its agents to be the first line of defense against the abuse of their services. As such, each agent and their associates have a critical role to play in the detection and prevention of ML/TF.
All Talk Remit agents must read, understand, and implement the requirements described in this ACP and the policies and procedures contained herein.
6.1 Training
Agent training is an important component of the ACP. Agent employees must understand the compliance requirements related to the transactions they perform as well understanding ML/TF methods and typologies, and how to detect suspicious activity.
Talk Remit provides all agents with training on the regulatory requirements applicable to the duties they perform on behalf of Talk Remit. All employees and management of entity agents who meet with customers, conduct transactions, or who complete any documentation related to transactions must also be trained.
Talk Remit meets this requirement in the following ways:
- All individual agents and entity agents’ employees must review the ACP at the on-set of the agent relationship; and
- All individual agents and entity agents’ employees must satisfactorily complete AML training at the on-set of the relationship and every year thereafter, including passing a quiz with a score of 80% or higher.
Training content includes:
- what ML and TF is;
- customer identification processes;
- record keeping requirements;
- penalties for non-compliance;
- internal policies and procedures and job-related responsibilities.
- examples of how the products and services offered by the agent are vulnerable to ML/TF abuses;
- individual legal responsibilities;
- monitoring for and reporting suspicious transactions, activity and behaviours to Talk Remit through the use of unusual transaction reports (“UTR”); and
- Non-disclosure of UTRs, to ensure agents are made aware that they cannot disclose that a suspicious transaction report (“STR”) may have been submitted, or disclose the contents of such a report, with the intent to prejudice a criminal investigation, whether it has started or not.
Agents must retain training logs (refer to Appendix A for a sample log) for themselves (if they are individual agents) and for each agent employee (for entity agents) for a minimum of five years from the date training was conducted. Training logs are subject to review by the MLRO or Agent Compliance Unit upon request.
6.2 Agent Responsibilities
6.2.1 Customer Onboarding and Due Diligence
Talk Remit is required to conduct customer due diligence including verifying the identity of the customer and collecting and recording certain information, both at the time of onboarding and periodically thereafter. These functions are completed automatically by Talk Remit and agents do not have any responsibility with respect to these activities, other than verifying the likeness of the ID photo image to the potential customer.
6.2.2 Regulatory Reporting
Talk Remit is required to submit regulatory reports to FINTRAC with respect to certain types of transactions. The MLRO or Agent Compliance Unit monitors all transactions conducted by the agent for the purpose of identifying those transactions that may require reporting to FINTRAC. Agents do not have any responsibility with respect to submitting reports directly to FINTRAC.
If an agent becomes aware of a transaction that is indicative of suspicious activity, it is the expectation of Talk Remit that the agent submits a UTR to the MLRO or Agent Compliance Unit as soon as possible, as described in Section 6.5.
6.2.3 Record Keeping and Retention
Canadian AML requires Talk Remit to keep certain records with respect to its customers, transactions and business activities. The majority of these records are created and maintained by Talk Remit.
Agents must ensure that all records maintained on behalf of Talk Remit are stored according to the following table.
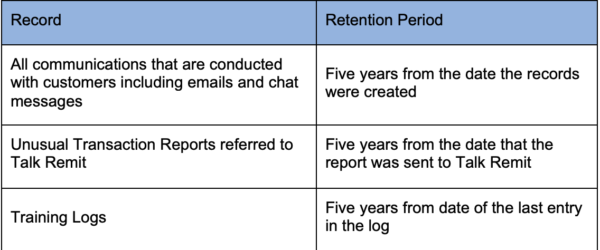
Talk Remit periodically makes requests for records and information collected or held as a function of conducting transactions as an agent of Talk Remit. These records may be required by an auditor, investigative agency, FINTRAC examiner, or the MLRO or Agent Compliance Unit.
The agent must provide Talk Remit any requested information within 48 hours of receiving the request (Monday thru Friday). Easy access to these records is vital.
Upon the termination of the relationship between the agent and Talk Remit, all records collected or held as a function of conducting transactions as an agent of Talk Remit must be returned to Talk Remit within 30 days.
6.3 Suspicious Transactions
A transaction is suspicious if, based on the information available to Talk Remit or the agent, there are reasonable grounds to suspect that a customer is not who they claim to be, or a transaction is involved in some way with the proceeds of crime or terrorist financing.
For the purposes of STRs, this includes, but is not limited to, any transaction or series of transactions that:
- represents the funds derived from any illegal activity, including matters such as corruption, tax evasion, fraud, robbery; and/or
- was conducted or attempted to be conducted in order to hide or disguise funds derived from illegal activities; and/or
- disguises or attempts to disguise, the true ownership, nature, source of funds, location or control of the illicit funds or assets; and or
- was conducted, or attempted to be conducted, to avoid transaction reporting requirements or any other law or regulation.
Suspicious transactions are also financial transactions or patterns of activity that the agent knows that they are in possession of funds or property that belong to a terrorist (either an individual or an organization) or believes that they are in possession of funds that belong to a listed person. A listed person means anyone on a list published in the of the Regulations Implementing the United Nations Resolutions on the Suppression of Terrorism issued under the United Nations Act.
In this context, property means any type of real or personal property. This includes any deed or instrument giving title or right to property or giving right to money or goods. For example, cash, bank accounts, insurance policies, money orders, real estate, securities, precious metals and stones, and traveler’s cheques, among other types of assets, are considered property.
Throughout this guideline, any mention of TF includes any transactions or activity related to terrorist financing, terrorist acts, a terrorist organization, an individual terrorist, or possession of terrorist property.
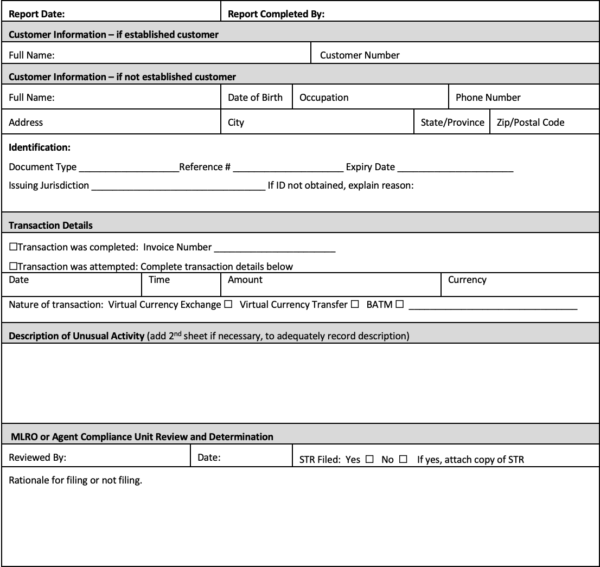
Agents are required to report anything that is unusual rather than trying to determine whether there are reasonable grounds to suspect. This is a very, very low threshold of suspicion and Talk Remit is reliant on its agents to complete a UTR (refer to Appendix B) each and every time that a slight suspicion is raised. The responsibility for determining whether there are reasonable grounds to suspect ML or TF, and for filing FINTRAC STRs, rests with Talk Remit.
Talk Remit must maintain records of the investigation and determination as well as all UTRs and STRs that have been filed.
6.3.1 How to Identify Unusual/Suspicious Transactions
Suspicious transactions are often detected because they are not the sort of transactions that a typical person or entity would be expected to conduct. It is important to consider the context of the transaction because what makes sense for one customer may be highly unusual for another. Agents should evaluate transactions in terms of what seems appropriate and is within normal practices.
Agents should pay special attention to transactions that:
- are complex or unusual;
- present an unusual pattern;
- have no apparent economic purpose;
Agents may learn that a customer was being investigated or has been arrested for a drug offence or has connections to terrorist activities through the media or other sources. All transactions related to that customer should prompt a UTR.
A transaction may have a number of factors that do not raise suspicion when considered individually, but together suggest that something is amiss. Often criminals keep the dollar values of transactions low in order to avoid attention. Remember, behaviour is suspicious, not people.
Agents can refer to FINTRAC guidance for more information about determining suspicion.
6.3.2 Unusual Transaction Report Process
Once an agent employee detects a transaction or activity that is unusual and may represent ML or TF, it must be reported to Talk Remit using the UTR form. These forms must be completed in full detail with everything that is known about the customer. The UTR should be completed on the same day as the unusual activity is identified. Agents must not let the customer know that they are filling out this form or discuss its contents with anyone other than the MLRO or Agent Compliance Unit.
Agents must send the UTR to Talk Remit within 24 hours of identification of the suspicious facts. Talk Remit must then make the determination as to whether is the transaction or activity warrants submitting an STR to FINTRAC.
UTRs must be emailed to the MLRO or Agent Compliance Unit at [email protected]. A copy of this report must be retained by the agent for five years.
6.3.3 Indicators of Unusual/Suspicious Transactions
FINTRAC has published ML/TF indicators that help identity transactions that may be unusual and should be reported to Talk Remit via a UTR. They include indicators based on certain characteristics that have been linked to money laundering or terrorist activities in the past.
The indicators have to be assessed in the context in which the transaction occurs or is attempted. What is suspicious for one customer, may represent normal activity for another customer. Therefore, its important to gather as much information as possible about the customer in order to gain a better understanding of the type of transactions that they can be expected to conduct.
Appendix C contains examples of common indicators of ML published by FINTRAC.
7 Forms, Reports and Documents
All agents are required to utilize forms, reports and documents provided by Talk Remit when conducting business on behalf of Talk Remit to ensure all the appropriate information has been collected, verified and maintained.
All forms, reports and documents are kept by Talk Remit for a minimum of five years after the date the relationship with the agent has ceased.
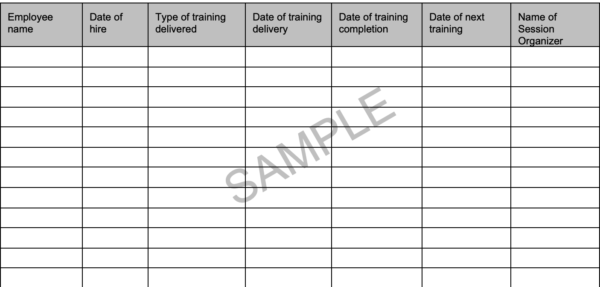
Appendix A – Sample Training Log
Agents are required to undergo annual training per the Agent Compliance Program. This is a sample log that agents can utilize to maintain training records.
- Agent must maintain this record;
- Agent must record all training events with full details;
- Agent must attach copies of completion certificates where available;
- This Log must be retained for five years from the date of the last entry; and
- This Log must be provided to Talk Remit upon request.
Appendix B – Unusual Transaction Report
Unusual Transaction Report
Appendix C – Suspicious Indicators [2]
In their STR Guidance, FINTRAC provides indicators which are instructive to the assessment of potentially suspicious activity.
ML/TF indicators related to identifying the person or entity
- There is an inability to properly identify the customer or there are questions surrounding the customer’s identity.
- The customer refuses or tries to avoid providing information required or provides information that is misleading, vague, or difficult to verify.
- The customer refuses to provide information or provides information that is false, conflicting, misleading or substantially incorrect.
- The identification presented by the customer cannot be verified (e.g. it is a copy).
- There are inconsistencies in the identification documents or different identifiers provided by the customer, such as address, date of birth or phone number.
- Customer produces seemingly false information or identification that appears to be counterfeited, altered or inaccurate.
- Customer displays a pattern of name variations from one transaction to another or uses aliases.
- Customer alters the transaction after being asked for identity documents.
- The customer provides only a non-civic address such as a post office box or disguises a post office box as a civic address for the purpose of concealing their physical residence.
- Common identifiers (e.g. addresses, phone numbers, etc.) used by multiple customers purchasing properties that do not appear to be related.
- Transactions involve individual(s) or entity(ies) identified by media, law enforcement and/or intelligence agencies as being linked to criminal activities.
- Attempts to verify the information provided by a new or prospective customer are difficult.
ML/TF indicators related to customer behaviour
- Customer makes statements about involvement in criminal activities.
- Evidence of untruthfulness on behalf of the customer (e.g. providing false or misleading information).
- Customer exhibits nervous behaviour.
- The customer refuses to provide information when required or is reluctant to provide information.
- Customer has a defensive stance to questioning.
- Customer presents confusing details about the transaction or knows few details about its purpose.
- Customer avoids contact with reporting entity employees.
- The customer refuses to identify a source for funds or provides information that is false, misleading, or substantially incorrect.
- The customer exhibits a lack of concern about higher than normal transaction costs or fees.
- Customer makes inquiries/statements indicating a desire to avoid reporting or tries to persuade the reporting entity not to file/maintain required reports.
- Insufficient explanation for source of funds.
ML/TF indicators related to the person/entity financial profile
- The transactional activity (level or volume) suddenly changes and/or is inconsistent with the customer’s apparent financial standing, their usual pattern of activities or occupational information (e.g. student, unemployed, social assistance, etc.).
- Rounded sum transactions atypical of what would be expected from the customer.
- Size or type of transactions atypical of what is expected from the customer.
- There is a sudden change in customer’s financial profile, pattern of activity or transactions.
- Customer uses multiple accounts at several financial institutions for no apparent reason.
- Suspected use of personal funds for business purposes, or vice-versa.
- Use of multiple foreign bank accounts for no apparent reason.
ML/TF indicators based on atypical transactional activity
- Transaction is unnecessarily complex for its stated purpose.
- Transaction consistent with publicly known trend in criminal activity.
- Transaction involves a suspected shell entity (an entity that does not have an economical or logical reason to exist).
ML/TF indicators related to transactions structured below the reporting or identification requirements
- Customer appears to be structuring amounts to avoid customer identification or reporting thresholds.
- Customer appears to be collaborating with others to avoid customer identification or reporting thresholds.
- Multiple transactions conducted below the reporting threshold within a short time period.
- Customer makes inquiries that would indicate a desire to avoid reporting.
- Customer exhibits knowledge of reporting thresholds.
ML/TF indicators related to transactions that involve non-Canadian jurisdictions
- Transactions with a person who lives in or an entity that operates out of a jurisdiction that is known to be at a higher risk to facilitate ML/TF.
- Transactions involving a person who lives in or an entity that operates out of a location of concern, which can include jurisdictions where there are ongoing conflicts (and periphery areas), countries with weak money laundering/terrorist financing controls, or countries with highly secretive banking or other transactional laws such as transfer limits set by a government.
- Transactions involving any countries deemed high risk or non-cooperative by the Financial Action Task Force.
Due to the ever-evolving nature of the ML/TF environment, high-risk jurisdictions and trends are often subject to change. To ensure that you are referencing accurate information, FINTRAC encourages you to research publicly available sources on a regular basis to support these ML/TF indicators as part of your STR program. There are multiple sources that identify jurisdictions of concern, including the FATF which publishes contextual information on high-risk jurisdictions in relation to their risk of money laundering and terrorist financing. You may also observe funds coming from or going to jurisdictions that are reported in the media as locations where terrorists operate/carry out attacks and/or where terrorists have a large support base (state sponsors or private citizens). Identifying high-risk jurisdictions or known trends can also be included as part of your risk-based approach and internal STR program.
ML/TF indicators related to use of other parties
In the course of a ‘normal’ real estate purchase or sale, there are a ‘normal’ number of parties who are engaging in the transaction, depending on the nature of the transaction at hand. For example, in the instance of a real estate purchase, there are generally two parties to the transaction: the individual(s) selling a property and the individual(s) purchasing the property.
Transactions that involve parties not typically associated with a transaction can present an elevated risk of money laundering and/or terrorist financing. These additional parties can be used to allow a criminal to avoid being identified or being linked to an asset. This section includes examples of how the involvement of other parties may be indicative of the structure of a criminal enterprise. Some examples of such other parties include the use of a third-party, nominee or gatekeeper.
Use of third-party
A third-party is any individual or entity that instructs someone to act on their behalf for a financial activity or transaction. There are some situations where there is an apparent and discernable rationale for the inclusion of the third-party in a transaction and this may not be suspicious. However, you may become suspicious in a situation where the reason for a third-party acting on behalf of another person or entity does not make sense based on what you know about the customer or the third-party. Use of third parties is one method that money launderers and terrorist financiers use to distance themselves from the proceeds of crime or source of criminally obtained funds. By relying on other parties to conduct transactions they can distance themselves from the transactions that can be directly linked to the suspected ML/TF offence. Some examples of ML/TF indicators related to the use of a third-party indicators can be found below.
- Unrelated parties with no apparent relation to the person/entity provide a deposit for the transaction.
- A customer conducts transaction while accompanied, overseen or directed by another party.
- Customer appears or states to be acting on behalf of another party.
Use of nominee
A nominee is a particular type of other party that is authorized to conduct transactions on behalf of a person of entity. There are legitimate reasons for relying on a nominee to conduct financial activity of behalf of someone else. However, this type of activity is particularly vulnerable to ML/TF as it is a common method used by criminals to distance themselves from the transactions that could be linked to suspected ML/TF offences. Below are some examples of ML/TF indicators relating to the misuse of nominees.
- An individual or entity other than the person or entity purchasing or selling property conducts the majority of the transaction activity which seems unnecessary or excessive.
- Customer is involved in a transaction that is suspicious but refuses or is unable to answer questions related to the transaction.
Use of gatekeeper
A gatekeeper is an individual who controls access to the financial system and can act on behalf of a customer. Such services can be abused so that criminals have access to the financial system without being identified. Gatekeepers may include lawyers, accountants and other professions which can access the financial system on behalf of a customer. While there are many transactions where it is ‘normal’ to have a gatekeeper represent the interests of a customer, such an appearance of normalcy can also be utilized to the advantage of criminals to provide the veneer of legitimacy to their transactions. The use of gatekeepers themselves is not an indicator of an ML/TF offence. However, entities should consider the following examples which can indicate misuse of the financial system access provided to gatekeepers.
- Gatekeeper avoids identifying their customer or disclosing their customer’s identity when such identification would be normal during the course of a transaction.
- Gatekeeper is willing to pay higher fees and seeks to conduct the transaction quickly when there is no apparent need for such expediency.
Indicators related to terrorism financing
In Canada, terrorist financing offences make it a crime to knowingly collect or provide property, which can include financial or other related services, for terrorist purposes. This section is focused on examples that are specific to the possible commission of a terrorist financing offence. However, please note that the other ML/TF indicators in this guidance may also prove relevant in determining when you have reasonable grounds to suspect the commission of terrorist financing as the methods used by criminals to evade detection of money laundering are similar.
Indicators specifically related to terrorist financing:
- Transactions with a person who lives in or an entity that operates out of certain high-risk jurisdictions such as locations in the midst of or in proximity to, armed conflict where terrorist groups operate or locations which are subject to weaker ML/TF controls.
- Customer identified by media or law enforcement as having travelled, attempted or intended to travel to high-risk jurisdictions (including cities or districts of concern), specifically countries (and adjacent countries) under conflict and/or political instability or known to support terrorist activities and organizations.
- Transactions involve individual(s) or entity(ies) identified by media and/or sanctions lists as being linked to a terrorist organization or terrorist activities.
- Law enforcement information provided which indicates individual(s) or entity(ies) may be linked to a terrorist organization or terrorist activities.
- Individual or entity states or eludes that they support violent extremism or radicalization.
- Customer provides multiple variations of name, address, phone number or additional identifiers.
ML/TF indicators specific to MSBs
In addition to the general ML/TF indicators, there may be more specific ML/TF indicators related to your MSB, including foreign exchange dealers, money remitters, issuers of traveller’s cheques, and agents of the Crown that sell or redeem money orders.
Below are some examples of sector specific ML/TF indicators that you should consider as part of your STR program.
- Customer requests a transaction at a foreign exchange rate that exceeds the posted rate.
- Customer wants to pay transaction fees that exceed the posted fees.
- Customer knows little about address and contact details for payee, is reluctant to disclose this information, or requests a bearer instrument.
- Customer enters into transactions with counter parties in locations that are unusual for the customer.
- Customer requests that a large amount of foreign currency be exchanged to another foreign currency.
[1] Any employee, officer, director, or agent who willfully or recklessly directed, authorized, acquiesced or participated in the commission of the offence can also be found guilty.
[2] http ://www.fintrac-canafe.gc.ca/guidance-directives/transaction-operation/indicators-indicateurs/msb_mltf-eng.asp